Engineers at Southwest Research Institute (SwRI), headquartered in San Antonio, Texas, have identified cybersecurity vulnerabilities in electric vehicles (EVs) using direct current fast-charging systems. These systems, which rely on power line communication (PLC) technology to transmit data between vehicles and charging equipment, were found to have significant security weaknesses.
In a laboratory setting, the SwRI team exploited vulnerabilities in the PLC layer, gaining access to network keys and digital addresses on both the chargers and the vehicles. Katherine Kozan, an engineer leading the project, noted that the PLC layer lacked encryption, leaving it poorly secured. The team discovered unsecured key generation on older chips, a known issue confirmed by online research.
This research is part of SwRI’s broader efforts to enhance automotive cybersecurity, building on a 2020 project where SwRI disrupted a J1772 charger using a lab-built spoofing device. The latest project focused on vehicle-to-grid (V2G) charging technologies governed by ISO 15118 specifications, which facilitate communication between EVs and electric vehicle supply equipment (EVSE) for power transfer.
Vic Murray, assistant director of SwRI’s high reliability systems department, emphasized the need to secure the grid infrastructure against cyberattacks as it adapts to accommodate more EVs: “As the grid evolves to take on more EVs, we need to defend our critical grid infrastructure against cyberattacks while also securing payments to charge EVs. Our research found room for improvements.”
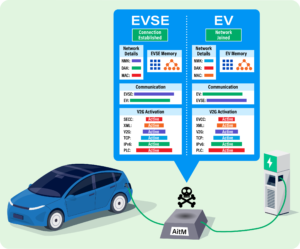
The SwRI team developed an adversary-in-the-middle (AitM) device with specialized software, allowing them to eavesdrop on traffic between EVs and EVSE for data collection and analysis. By identifying the media access control addresses of the EV and EVSE, the team pinpointed the network membership key, which facilitates network access and traffic monitoring. FJ Olugbodi, an engineer at SwRI, suggested that encrypting the network membership key could enhance the security of the V2G charging process, preventing destructive attacks such as firmware corruption.
However, implementing encryption in embedded vehicle systems presents challenges, as additional layers of encryption and authentication could potentially disrupt vehicle functionality. SwRI has developed a zero-trust architecture aiming to address these issues, connecting various embedded systems through a single cybersecurity protocol. Future research will test zero-trust systems for PLC and other network layers.
Cameron Mott, a manager overseeing automotive cybersecurity research, commented, “Automotive cybersecurity poses many layers of complexity, but we are excited about these new techniques to identify and address vulnerabilities”.